Free CompTIA SY0-601 Exam Dumps - Page 5
MultipleChoice
A security analyst Is investigating multiple hosts that are communicating to external IP addresses during the hours of 2:00 a.m, - 4:00 a.m, The malware has evaded detection by traditional antivirus software. Which of the
following types of malware Is MOST likely infecting the hosts?
OptionsMultipleChoice
The Chief Information Security Officer directed a nsk reduction in shadow IT and created a policy requiring all unsanctioned high-nsk SaaS applications to be blocked from user access Which of the following is the BEST security solution to reduce this risk?
OptionsMultipleChoice
A Chief Executive Officer (CEO) is dissatisfied with the level of service from the company's new service provider. The service provider is preventing the CEO.
from sending email from a work account to a personal account. Which of the following types of service providers is being used?
OptionsMultipleChoice
n organization plans to transition the intrusion detection and prevention techniques on a critical subnet to an anomaly-based system. Which of the following does the organization
need to determine for this to be successful?
OptionsDragDrop
An attack has occurred against a company.
INSTRUCTIONS
You have been tasked to do the following:
Identify the type of attack that is occurring on the network by clicking on the attacker's tablet and reviewing the output. (Answer Area 1).
Identify which compensating controls should be implemented on the assets, in order to reduce the effectiveness of future attacks by dragging them to the correct server.
(Answer area 2) All objects will be used, but not all placeholders may be filled. Objects may only be used once.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
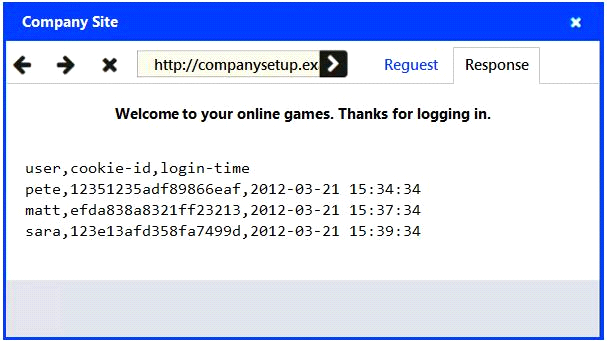

























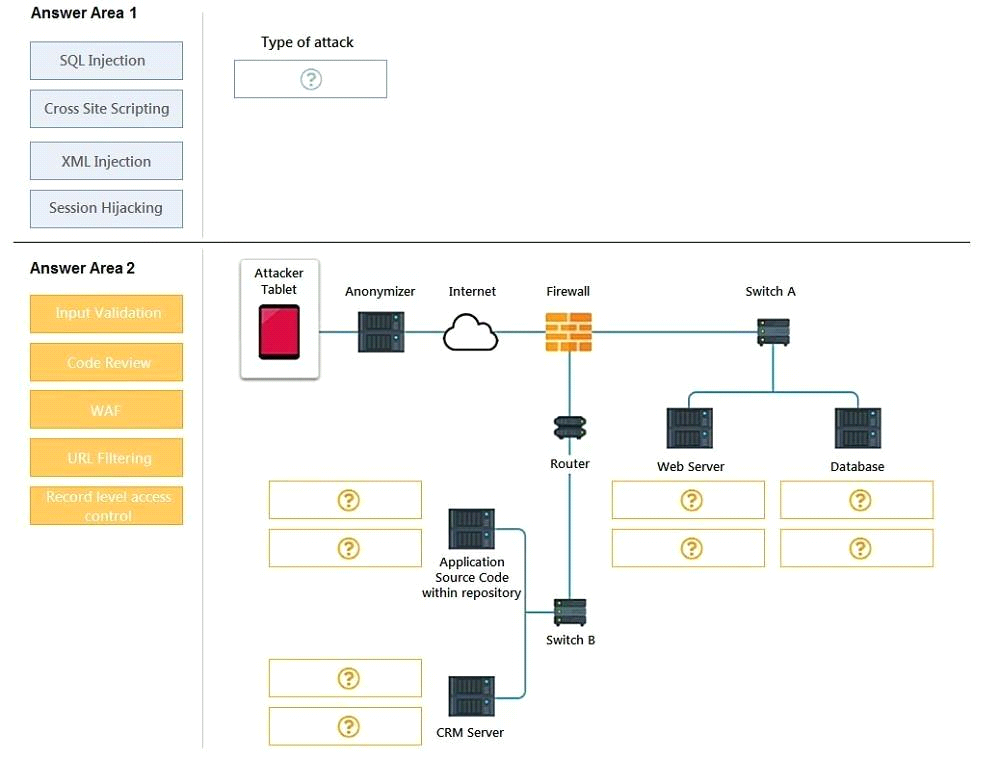

























MultipleChoice
An attacker was easily able to log in to a company's security camera by performing a baste online search for a setup guide for that particular camera brand and model. Which of the following BEST describes the configurations the attacker exploited?
A Weak encryption
OptionsHotspot
SIMULATION
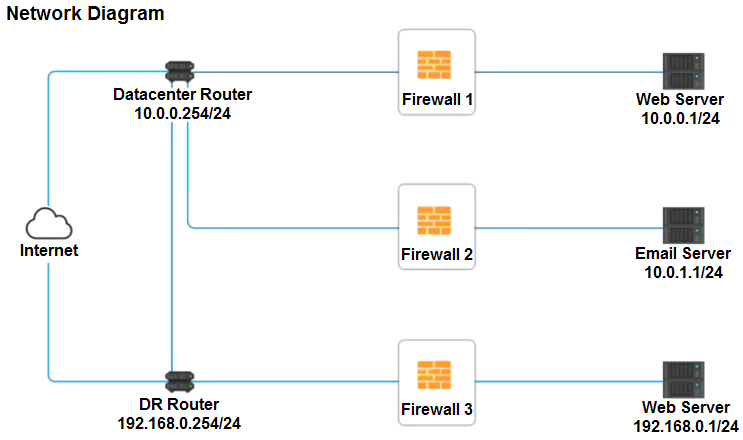
A company recently added a DR site and is redesigning the network. Users at the DR site are having issues browsing websites.
INSTRUCTIONS
Click on each firewall to do the following:
Deny cleartext web traffic.
Ensure secure management protocols are used.
Resolve issues at the DR site.
The ruleset order cannot be modified due to outside constraints.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
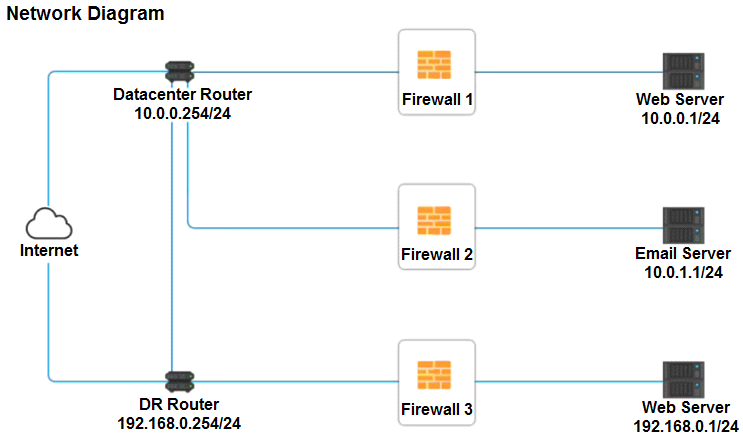
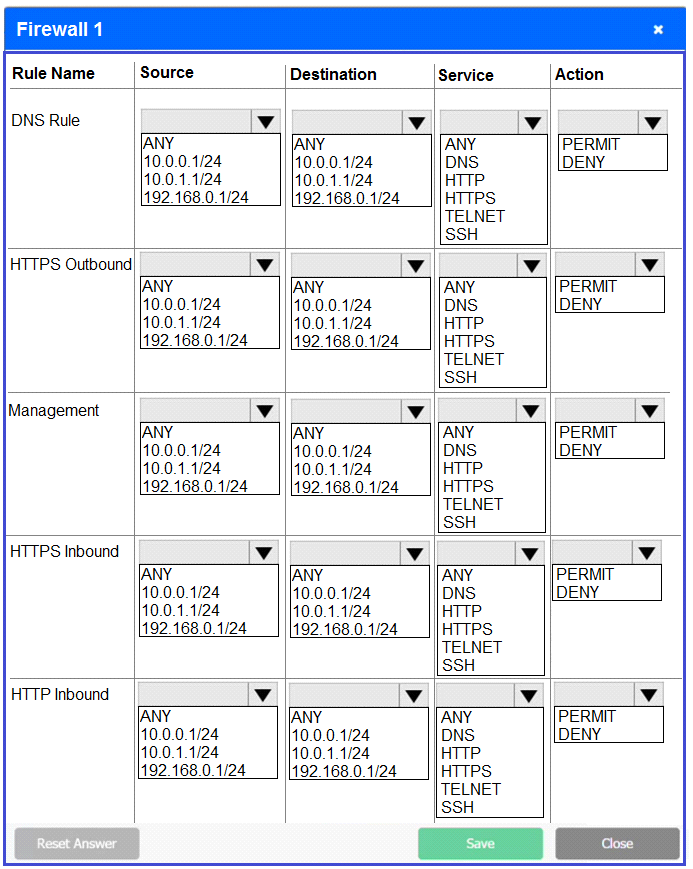
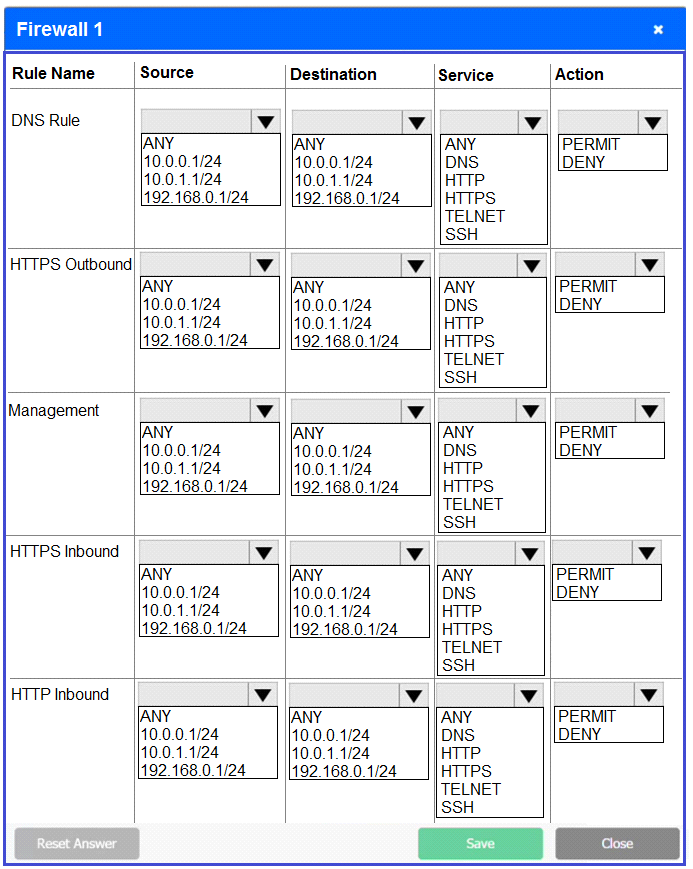
Firewall 1:
DNS Rule -- ANY --> ANY --> DNS --> PERMIT
HTTPS Outbound -- 10.0.0.1/24 --> ANY --> HTTPS --> PERMIT
Management -- ANY --> ANY --> SSH --> PERMIT
HTTPS Inbound -- ANY --> ANY --> HTTPS --> PERMIT
HTTP Inbound -- ANY --> ANY --> HTTP --> DENY
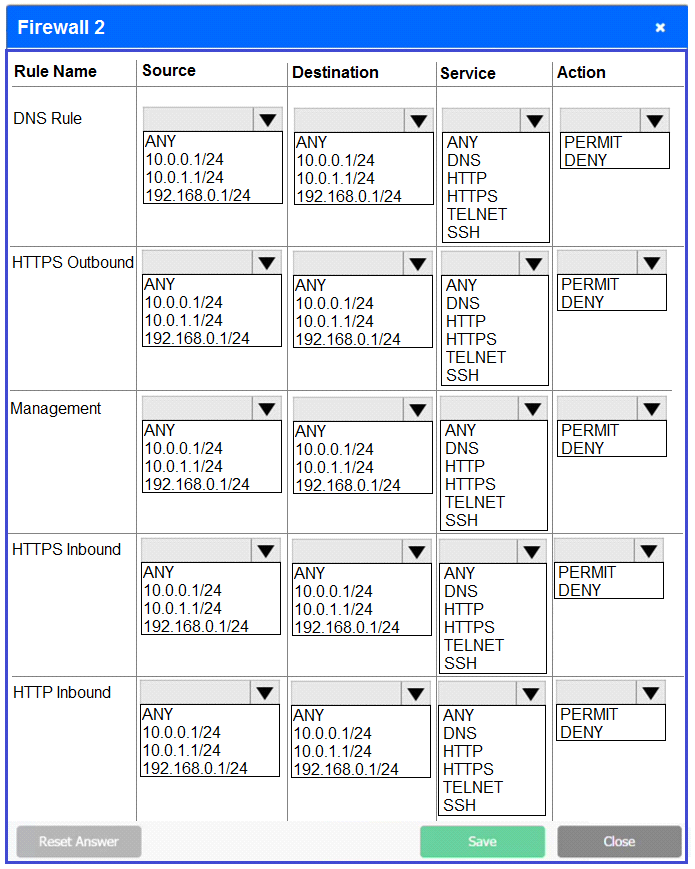
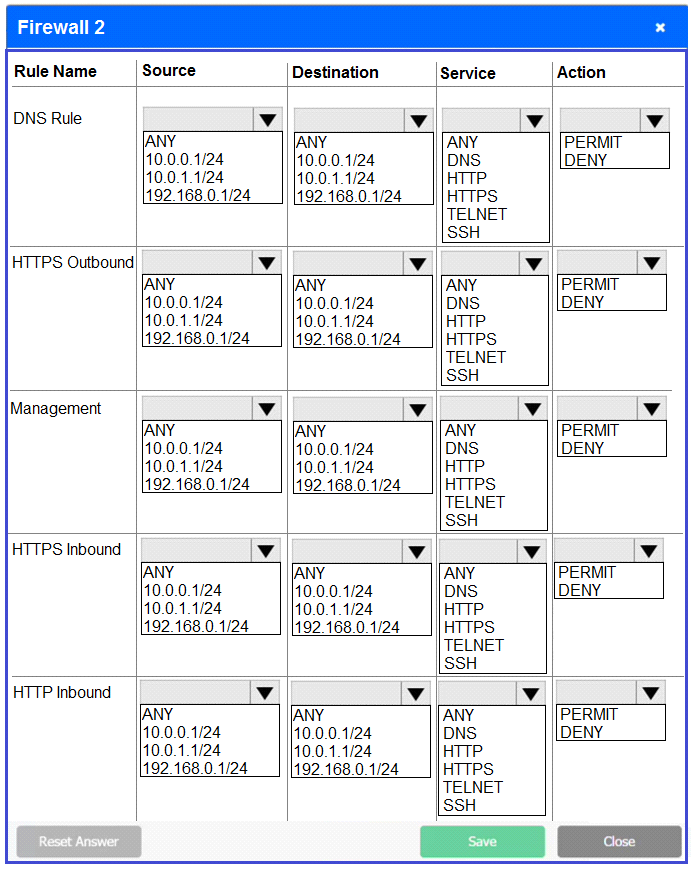
Firewall 2: No changes should be made to this firewall
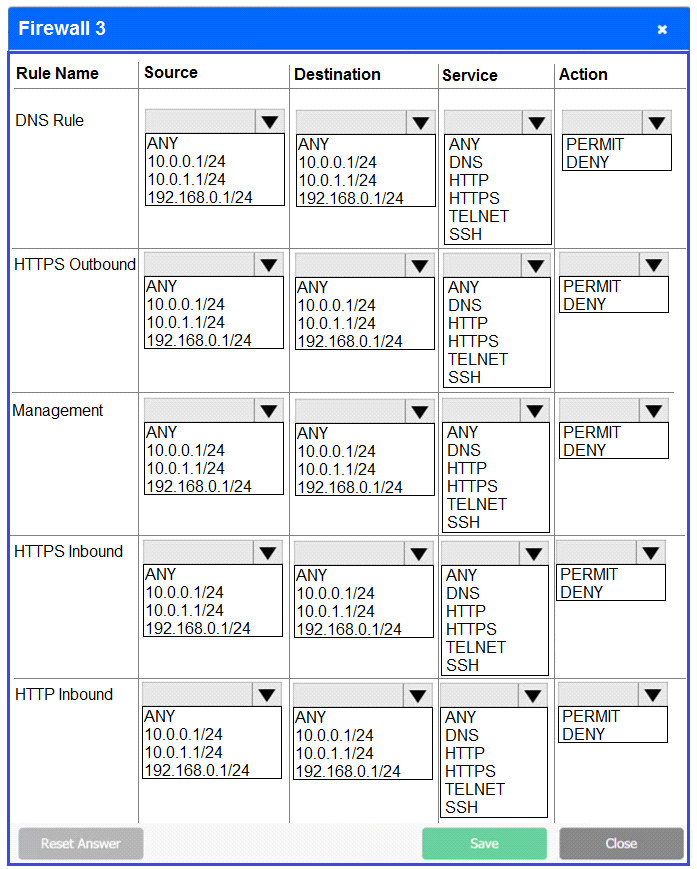
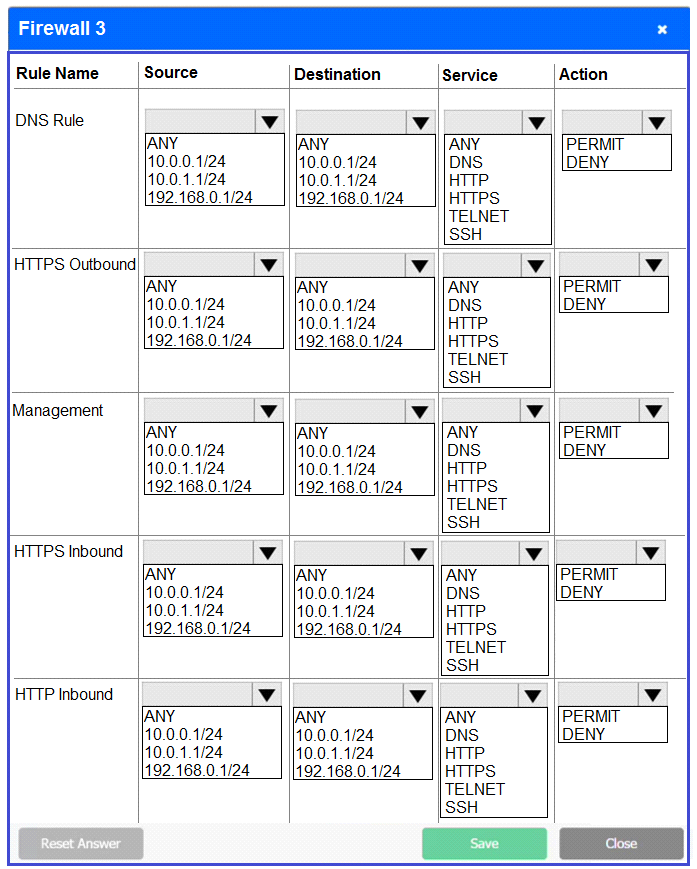
Firewall 3:
DNS Rule -- ANY --> ANY --> DNS --> PERMIT
HTTPS Outbound -- 192.168.0.1/24 --> ANY --> HTTPS --> PERMIT
Management -- ANY --> ANY --> SSH --> PERMIT
HTTPS Inbound -- ANY --> ANY --> HTTPS --> PERMIT
HTTP Inbound -- ANY --> ANY --> HTTP --> DENY
MultipleChoice
A157
is given the following, requirements?
* The solution must be inline in the network
* The solution must be able to block known malicious traffic
* The solution must be able to stop network-based attacks
Which of the following should the network administrator implement to BEST meet these requirements?
OptionsMultipleChoice
The process of passively gathering information poor to launching a cyberattack is called:
OptionsMultipleChoice
SIMULATION
A company recently added a DR site and is redesigning the network. Users at the DR site are having issues browsing websites.
INSTRUCTIONS
Click on each firewall to do the following:
Deny cleartext web traffic.
Ensure secure management protocols are used.
Resolve issues at the DR site.
The ruleset order cannot be modified due to outside constraints.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.