Free CompTIA SY0-601 Exam Dumps - Page 2
MultipleChoice
Which of the following components can be used to consolidate and forward inbound Internet traffic to multiple cloud environments though a single firewall?
OptionsMultipleChoice
A company is receiving emails with links to phishing sites that look very similar to the company's own website address and content. Which of the following is the BEST way for the company to mitigate this attack?
OptionsMultipleChoice
A company labeled some documents with the public sensitivity classification This means the documents can be accessed by:
OptionsMultipleChoice
A security engineer was assigned to implement a solution to prevent attackers from gaining access by pretending to be authorized users. Which of the following technologies meets the requirement?
OptionsMultipleChoice
A company recently experienced a significant data loss when proprietary Information was leaked to a competitor. The company took special precautions by using proper labels; however, email filter logs do not have any record of the incident. An Investigation confirmed the corporate network was not breached, but documents were downloaded from an employee's COPE tablet and passed to the competitor via cloud storage. Which of the following is the BEST mitigation strategy to prevent this from happening in the future?
OptionsMultipleChoice
Which of the following is the MOST relevant security check to be performed before embedding third-parry libraries in developed code?
OptionsMultipleChoice
The Chief Information Security Officer (CISO) has requested that a third-party vendor provide supporting documents that show proper controls are in place to protect customer dat
a. Which of the following would be BEST for the third-party vendor to provide to the CISO?
OptionsMultipleChoice
A recent audit cited a risk involving numerous low-criticality vulnerabilities created by a web application using a third-party library. The development staff state there are still customers using the application even though it is end of life and it would be a substantial burden to update the application for compatibility with more secure libraries. Which of the following would be the MOST prudent course of action?
OptionsMultipleChoice
A security analyst is investigating suspicious traffic on the web server located at IP address 10.10.1.1. A search of the WAF logs reveals the following output:
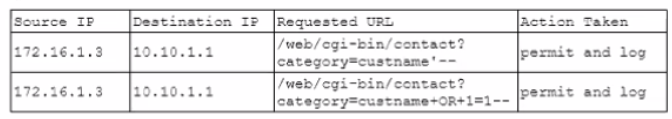
Which of the following is MOST likely occurring?
OptionsMultipleChoice
Due to unexpected circumstances, an IT company must vacate its main office, forcing all operations to alternate, off-site locations. Which of the following will the company MOST likely reference for guidance during this change?
Options
