Free CompTIA SY0-601 Exam Dumps - Page 3
MultipleChoice
A security proposal was set up to track requests for remote access by creating a baseline of the users' common sign-in properties. When a baseline deviation is detected, an Iv1FA challenge will be triggered. Which of the following should be configured in order to deploy the proposal?
OptionsMultipleChoice
Which of the following are common VoIP-associated vulnerabilities? (Select TWO).
OptionsMultipleChoice
During a trial, a judge determined evidence gathered from a hard drive was not admissible. Which of the following BEST explains this reasoning?
OptionsMultipleChoice
A SOC operator is analyzing a log file that contains the following entries:
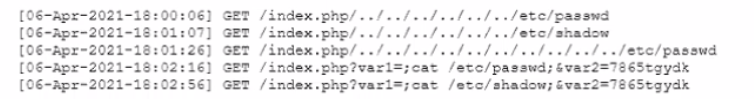
MultipleChoice
Which of the following control Types would be BEST to use in an accounting department to reduce losses from fraudulent transactions?
OptionsMultipleChoice
The database administration team is requesting guidance for a secure solution that will ensure confidentiality of cardholder data at rest only in certain fields in the database schem
a. The requirement is to substitute a sensitive data field with a non-sensitive field that is rendered useless if a data breach occurs Which of the following is the BEST solution to meet the requirement?
OptionsMultipleChoice
A DBA reports that several production server hard drives were wiped over the weekend. The DBA also reports that several Linux servers were unavailable due to system files being deleted unexpectedly. A security analyst verified that software was configured to delete data deliberately from those servers. No backdoors to any servers were found. Which of the following attacks was MOST likely used to cause the data toss?
OptionsMultipleChoice
A company is implementing BYOD and wants to ensure all users have access to the same cloud-based services. Which of the following would BEST allow the company to meet this requirement?
OptionsMultipleChoice
Which of the following documents provides expectations at a technical level for quality, availability, and responsibilities?
OptionsMultipleChoice
A security analyst is receiving numerous alerts reporting that the response time of an internet-facing application has been degraded However, the internal network performance was not degraded. Which of the following MOST likely explains this behavior?
Options
