Free CompTIA SY0-601 Exam Dumps - Page 4
MultipleChoice
DRAG DROP - A security engineer is setting up passwordless authentication for the first time. INSTRUCTIONS - Use the minimum set of commands to set this up and verify that it works. Commands cannot be reused. If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
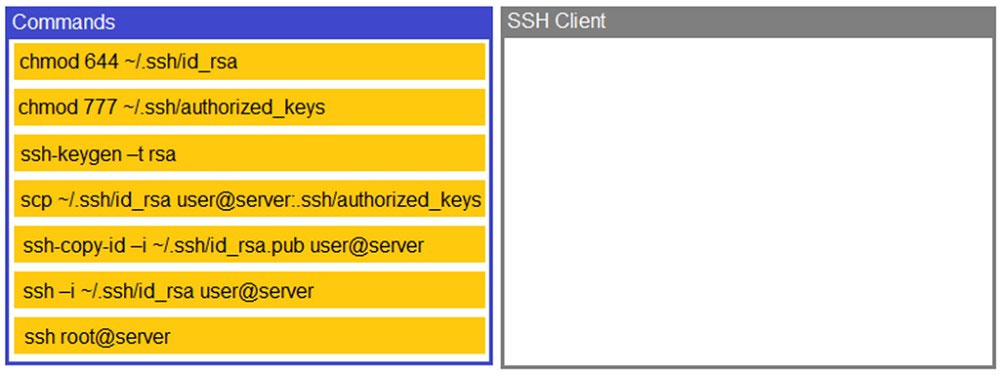
1. ssh-keygen -t rsa (creating the key-pair)
2. ssh-copy-id -i /.ssh/id_rsa.pub user@server (copy the public-key to user@server)
3. ssh -i ~/.ssh/id_rsa user@server (login to remote host with private-key)
A small business just recovered from a ransomware attack against its file servers by purchasing the decryption keys from the attackers. The issue was triggered by a phishing email and the IT administrator wants to ensure it does not happen again. Which of the following should the IT administrator do FIRST after recovery?
OptionsMultipleChoice
Which of the following vulnerabilities is the attacker trying to exploit?
OptionsHotspot
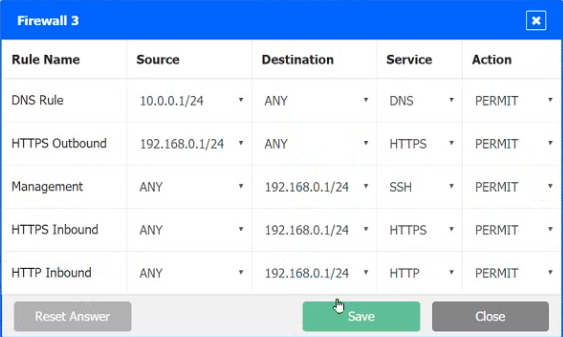
A company recently added a DR site and is redesigning the network. Users at the DR site are having issues browsing websites.
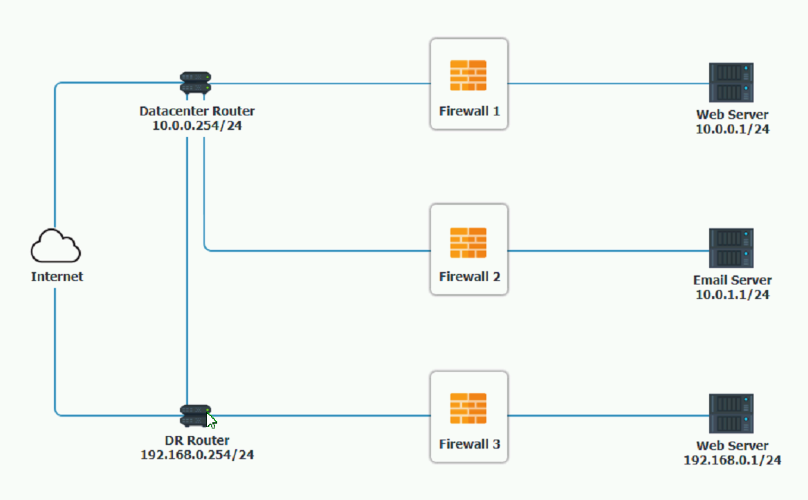
INSTRUCTIONS
Click on each firewall to do the following:
1. Deny cleartext web traffic
2. Ensure secure management protocols are used.
3. Resolve issues at the DR site.
The ruleset order cannot be modified due to outside constraints.
Hat any time you would like to bring back the initial state of the simulation, please dick the Reset All button.
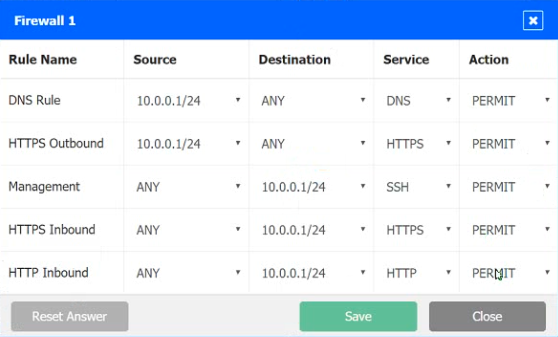
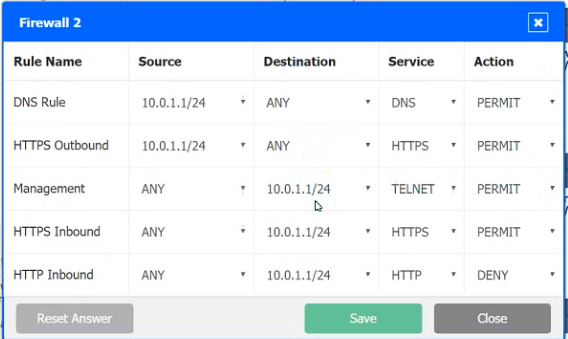
MultipleChoice
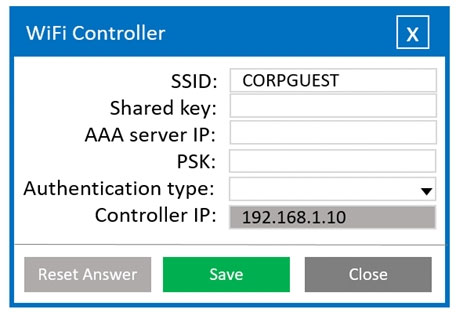
A systems administrator needs to install a new wireless network for authenticated guest access. The wireless network should support 802. IX using the most secure encryption and protocol available.
Perform the following steps:
1. Configure the RADIUS server.
2. Configure the WiFi controller.
3. Preconfigure the client for an
incoming guest. The guest AD
credentials are:
User: guest01
Password: guestpass
DragDrop
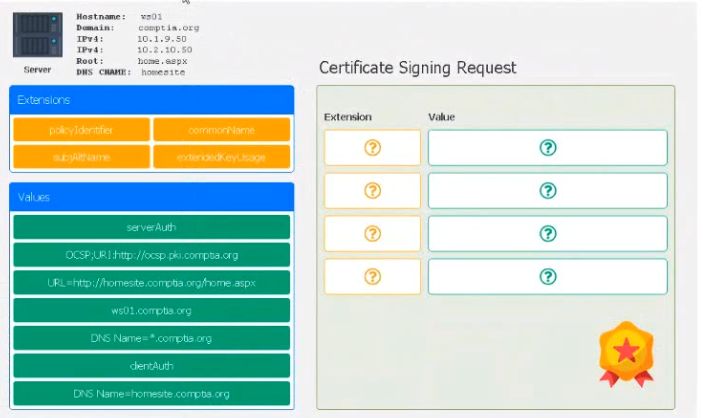
Leveraging the information supplied below, complete the CSR for the server to set up TLS (HTTPS)
* Hostname: ws01
* Domain: comptia.org
* IPv4: 10.1.9.50
* IPV4: 10.2.10.50
* Root: home.aspx
* DNS CNAME:homesite.
Instructions:
Drag the various data points to the correct locations within the CSR. Extension criteria belong in the let hand column and values belong in the corresponding row in the right hand column.
























































































A security administrator needs to add fault tolerance and load balancing to the connection from the file server to the backup storage. Which of the following is the best choice to achieve this objective?
MultipleChoice
A new security engineer has started hardening systems. One of the hardening techniques the engineer is using involves disabling remote logins to the NAS. Users are now reporting the inability to use SCP to transfer files to the NAS, even though the data is still viewable from the users' PCs. Which of the following is the MOST likely cause of this issue?
A TFTP was disabled on the local hosts
OptionsHotspot
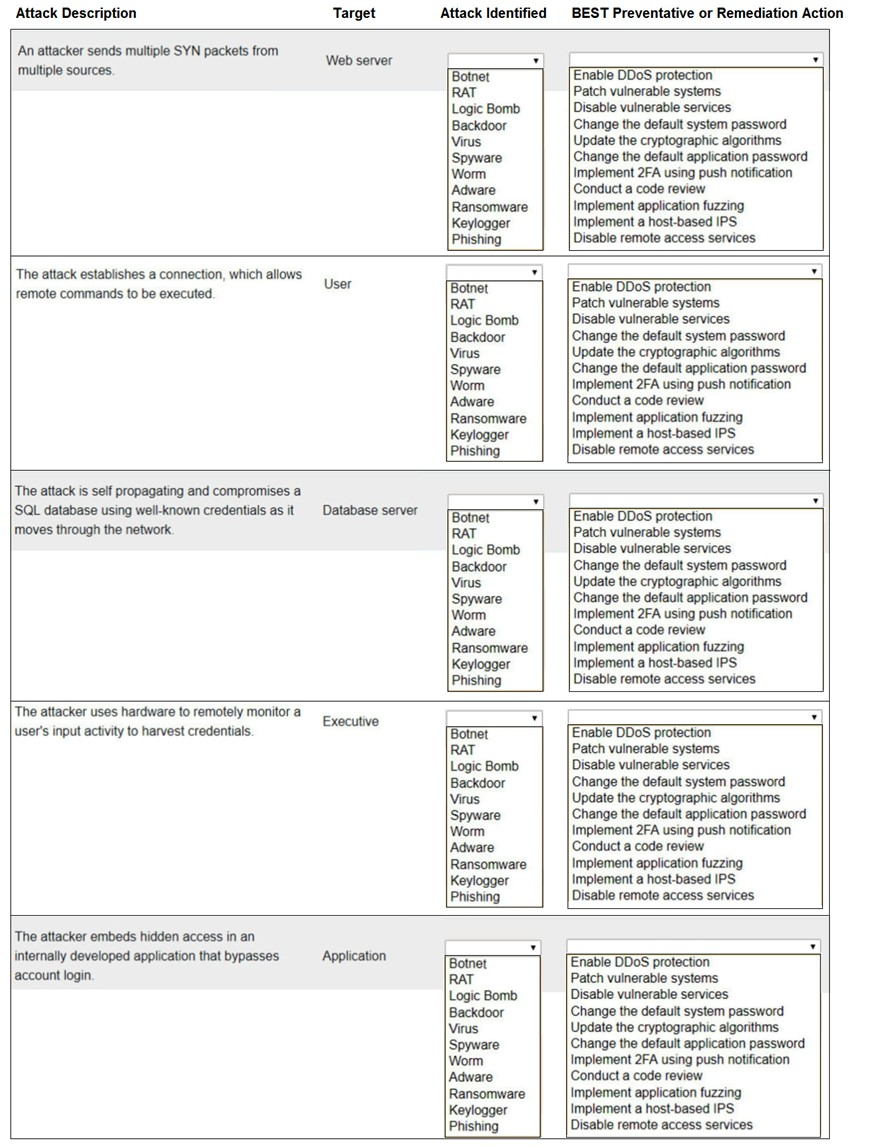
Select the appropriate attack and remediation from each drop-down list to label the corresponding attack with its remediation.
INSTRUCTIONS
Not all attacks and remediation actions will be used.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
MultipleChoice
A new security engineer has started hardening systems. One of the hardening techniques the engineer is using involves disabling remote logins to the NAS. Users are now reporting the inability to use SCP to transfer files to the NAS, even though the data is still viewable from the users' PCs. Which of the following is the MOST likely cause of this issue?
A TFTP was disabled on the local hosts
OptionsMultipleChoice
DRAG DROP
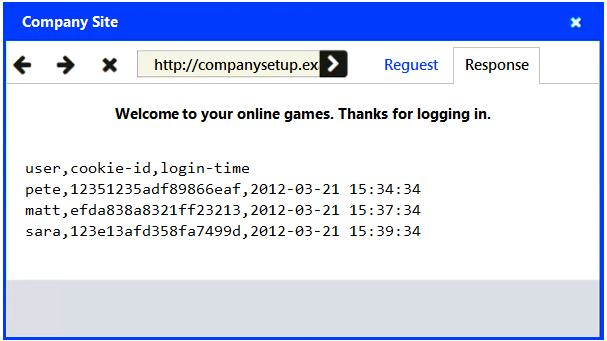
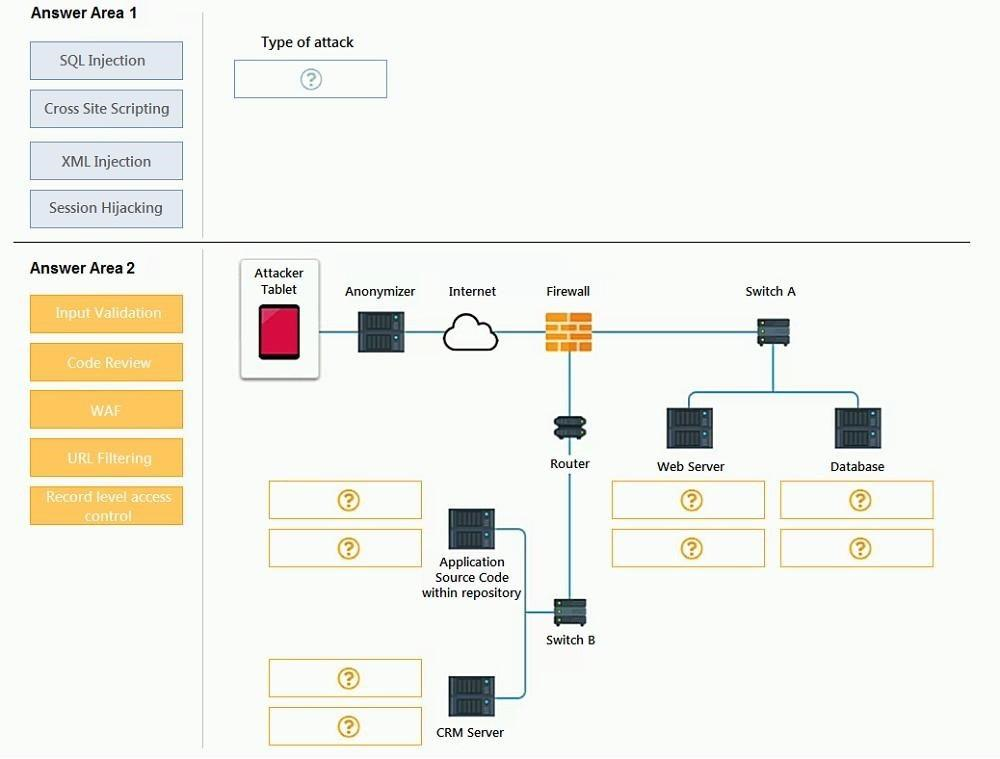
An attack has occurred against a company.
INSTRUCTIONS
You have been tasked to do the following:
Identify the type of attack that is occurring on the network by clicking on the attacker's tablet and reviewing the output. (Answer Area 1).
Identify which compensating controls should be implemented on the assets, in order to reduce the effectiveness of future attacks by dragging them to the correct server.
(Answer area 2) All objects will be used, but not all placeholders may be filled. Objects may only be used once.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
MultipleChoice
A company recently experienced a significant data loss when proprietary Information was leaked to a competitor. The company took special precautions by using proper labels; however, email filter logs do not have any record of the incident. An Investigation confirmed the corporate network was not breached, but documents were downloaded from an employee's COPE tablet and passed to the competitor via cloud storage. Which of the following is the BEST remediation for this data leak?
Options
