Free Eccouncil ECSAv10 Exam Dumps
Here you can find all the free questions related with Eccouncil Certified Security Analyst (ECSA) v10 (ECSAv10) exam. You can also find on this page links to recently updated premium files with which you can practice for actual Eccouncil Certified Security Analyst (ECSA) v10 Exam. These premium versions are provided as ECSAv10 exam practice tests, both as desktop software and browser based application, you can use whatever suits your style. Feel free to try the Certified Security Analyst (ECSA) v10 Exam premium files for free, Good luck with your Eccouncil Certified Security Analyst (ECSA) v10 Exam.MultipleChoice
George is a senior security analyst working for a state agency in Florid
a. His state's congress just passed a billmandating every state agency to undergo a security audit annually. After learning what will be required, Georgeneeds to implement an IDS as soon as possible before the first audit occurs.
The state bill requires that an IDSwith a "time-based induction machine" be used. What IDS feature must George implement to meet thisrequirement?
OptionsMultipleChoice
You are a security analyst performing a penetration tests for a company in the Midwest. After some initial reconnaissance, you discover the IP addresses of some Cisco routers used by the company. You type in the following URL that includes the IP address of one of the routers:
After typing in this URL, you are presented with the entire configuration file for that router. What have you discovered?
OptionsMultipleChoice
A pen tester has extracted a database name by using a blind SQL injection. Now he begins to test the table inside the database using the below query and finds the table:
What is the table name?
OptionsMultipleChoice
What is the maximum value of a ''tinyint'' field in most database systems?
OptionsMultipleChoice
Security auditors determine the use of WAPs on their networks with Nessus vulnerability scanner which identifies the commonly used WAPs.
One of the plug-ins that the Nessus Vulnerability Scanner uses is ID #11026 and is named ''Access Point Detection''. This plug-in uses four techniques to identify the presence of a WAP.
Which one of the following techniques is mostly used for uploading new firmware images while upgrading the WAP device?
OptionsMultipleChoice
What is a good security method to prevent unauthorized users from "tailgating"?
OptionsMultipleChoice
What is kept in the following directory? HKLM\SECURITY\Policy\Secrets
OptionsMultipleChoice
SQL injection attack consists of insertion or "injection" of either a partial or complete SQL query via the data input or transmitted from the client (browser) to the web application. A successful SQL injection attack can:
i) Read sensitive data from the database
iii) Modify database data (insert/update/delete)
iii) Execute administration operations on the database (such as shutdown the DBMS) iV) Recover the content of a given file existing on the DBMS file system or write files into the file system v) Issue commands to the operating system
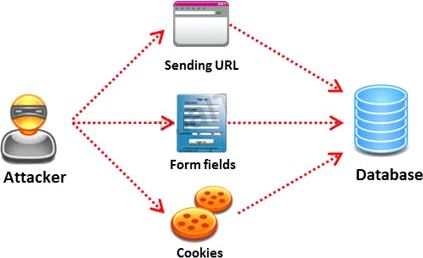
Pen tester needs to perform various tests to detect SQL injection vulnerability. He has to make a list of all input fields whose values could be used in crafting a SQL query, including the hidden fields of POST requests and then test them separately, trying to interfere with the query and to generate an error.
In which of the following tests is the source code of the application tested in a non-runtime environment to detect the SQL injection vulnerabilities?
OptionsMultipleChoice
One needs to run ''Scan Server Configuration'' tool to allow a remote connection to Nessus from the remote Nessus clients. This tool allows the port and bound interface of the Nessus daemon to be configured.
By default, the Nessus daemon listens to connections on which one of the following?
Options
