Free Eccouncil 312-50v11 Exam Dumps
Here you can find all the free questions related with Eccouncil Certified Ethical Hacker V11 (312-50v11) exam. You can also find on this page links to recently updated premium files with which you can practice for actual Eccouncil Certified Ethical Hacker V11 Exam. These premium versions are provided as 312-50v11 exam practice tests, both as desktop software and browser based application, you can use whatever suits your style. Feel free to try the Certified Ethical Hacker V11 Exam premium files for free, Good luck with your Eccouncil Certified Ethical Hacker V11 Exam.MultipleChoice
Which of the following web vulnerabilities would an attacker be attempting to exploit if they delivered the following input?
OptionsMultipleChoice
Joseph was the Web site administrator for the Mason Insurance in New York, who's main Web site was located at www.masonins.com. Joseph uses his laptop computer regularly to administer the Web site. One night, Joseph received an urgent phone call from his friend, Smith. According to Smith, the main Mason Insurance web site had been vandalized! All of its normal content was removed and replaced with an attacker's message ''Hacker Message: You are dead! Freaks!'' From his office, which was directly connected to Mason Insurance's internal network, Joseph surfed to the Web site using his laptop. In his browser, the Web site looked completely intact.

After seeing the defaced Web site, he disconnected his dial-up line, reconnected to the internal network, and used Secure Shell (SSH) to log in directly to the Web server. He ran Tripwire against the entire Web site, and determined that every system file and all the Web content on the server were intact. How did the attacker accomplish this hack?
OptionsMultipleChoice
What is the following command used for?
OptionsMultipleChoice
Joseph was the Web site administrator for the Mason Insurance in New York, who's main Web site was located at www.masonins.com. Joseph uses his laptop computer regularly to administer the Web site. One night, Joseph received an urgent phone call from his friend, Smith. According to Smith, the main Mason Insurance web site had been vandalized! All of its normal content was removed and replaced with an attacker's message ''Hacker Message: You are dead! Freaks!'' From his office, which was directly connected to Mason Insurance's internal network, Joseph surfed to the Web site using his laptop. In his browser, the Web site looked completely intact.
No changes were apparent. Joseph called a friend of his at his home to help troubleshoot the problem. The Web site appeared defaced when his friend visited using his DSL connection. So, while Smith and his friend could see the defaced page, Joseph saw the intact Mason Insurance web site. To help make sense of this problem, Joseph decided to access the Web site using hisdial-up ISP. He disconnected his laptop from the corporate internal network and used his modem to dial up the same ISP used by Smith. After his modem connected, he quickly typed www.masonins.com in his browser to reveal the following web page:
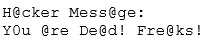
After seeing the defaced Web site, he disconnected his dial-up line, reconnected to the internal network, and used Secure Shell (SSH) to log in directly to the Web server. He ran Tripwire against the entire Web site, and determined that every system file and all the Web content on the server were intact. How did the attacker accomplish this hack?
OptionsMultipleChoice
Attempting an injection attack on a web server based on responses to True/False Question:s is called which of
the following?
OptionsMultipleChoice
A company's policy requires employees to perform file transfers using protocols which encrypt traffic. You suspect some employees are still performing file transfers using unencrypted protocols because the employees do not like changes. You have positioned a network sniffer to capture traffic from the laptops used by employees in the data ingest department. Using Wire shark to examine the captured traffic, which command can be used as a display filter to find unencrypted file transfers?
OptionsMultipleChoice
During the process of encryption and decryption, what keys are shared?
During the process of encryption and decryption, what keys are shared?
OptionsMultipleChoice
SQL injection (SOU) attacks attempt to inject SOL syntax into web requests, which may Bypass authentication and allow attackers to access and/or modify data attached to a web application.
Which of the following SQLI types leverages a database server's ability to make DNS requests to pass data to an attacker?
OptionsMultipleChoice
Attempting an injection attack on a web server based on responses to True/False Question: 01s is called which of the following?
OptionsMultipleChoice
Techno Security Inc. recently hired John as a penetration tester. He was tasked with identifying open ports in the target network and determining whether the ports are online and any firewall rule sets are encountered. John decided to perform a TCP SYN ping scan on the target network. Which of the following Nmap commands must John use to perform the TCP SVN ping scan?
Options
