Free CompTIA CS0-002 Exam Dumps
Here you can find all the free questions related with CompTIA Cybersecurity Analyst (CySA+) (CS0-002) exam. You can also find on this page links to recently updated premium files with which you can practice for actual CompTIA Cybersecurity Analyst (CySA+) Exam. These premium versions are provided as CS0-002 exam practice tests, both as desktop software and browser based application, you can use whatever suits your style. Feel free to try the CompTIA Cybersecurity Analyst (CySA+) Exam premium files for free, Good luck with your CompTIA Cybersecurity Analyst (CySA+) Exam.MultipleChoice
A security manager has asked an analyst to provide feedback on the results of a penetration lest. After reviewing the results the manager requests information regarding the possible exploitation of vulnerabilities Much of the following information data points would be MOST useful for the analyst to provide to the security manager who would then communicate the risk factors to senior management? (Select TWO)
OptionsMultipleChoice
A security analyst suspects a malware infection was caused by a user who downloaded malware after clicking
Error! Hyperlink reference not valid. in a phishing email.
To prevent other computers from being infected by the same malware variation, the analyst should create a rule on the .
OptionsMultipleChoice
An organization suspects it has had a breach, and it is trying to determine the potential impact. The organization knows the following:
* The source of the breach is linked to an IP located in a foreign country.
* The breach is isolated to the research and development servers.
* The hash values of the data before and after the breach are unchanged.
* The affected servers were regularly patched, and a recent scan showed no vulnerabilities.
Which of the following conclusions can be drawn with respect to the threat and impact? (Choose two.)
OptionsMultipleChoice
Ann, a user, reports to the security team that her browser began redirecting her to random sites while using her Windows laptop. Ann further reports that the OS shows the C: drive is out of space despite having plenty of space recently. Ann claims she not downloaded anything. The security team obtains the laptop and begins to investigate, noting the following:
* File access auditing is turned off.
* When clearing up disk space to make the laptop functional, files that appear to be cached web pages are immediately created in a temporary directory, filling up the available drive space.
* All processes running appear to be legitimate processes for this user and machine.
* Network traffic spikes when the space is cleared on the laptop.
* No browser is open.
Which of the following initial actions and tools would provide the BEST approach to determining what is happening?
OptionsMultipleChoice
A security analyst is investigating a malware infection that occurred on a Windows system. The system was not connected to a network and had no wireless capability Company policy prohibits using portable media or mobile storage The security analyst is trying to determine which user caused the malware to get onto the system Which of the following registry keys would MOST likely have this information?
A)
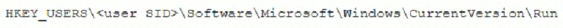
B)
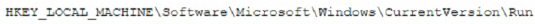
C)
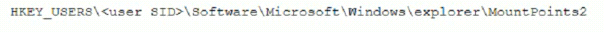
D)
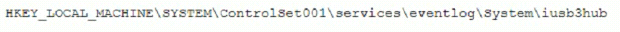
MultipleChoice
A security analyst suspects a malware infection was caused by a user who downloaded malware after clicking
To prevent other computers from being infected by the same malware variation, the analyst should create a rule on the .
OptionsMultipleChoice
While investigating an incident in a company's SIEM console, a security analyst found hundreds of failed SSH login attempts, which all occurred in rapid succession. The failed attempts were followed by a successful login on the root user Company policy allows systems administrators to manage their systems only from the company's internal network using their assigned corporate logins. Which of the following are the BEST actions the analyst can take to stop any further compromise? (Select TWO).
OptionsMultipleChoice
A custom script monitors real-time
OptionsMultipleChoice
While reviewing log files, a security analyst uncovers a brute-force attack that is being performed against an external webmail portal. Which of the following would be BEST to prevent this type of attack from beinq successful1?
OptionsMultipleChoice
Which indicators can be used to detect further occurrences of a data exfiltration incident. The analyst determines backups were not performed during this time and reviews the following:
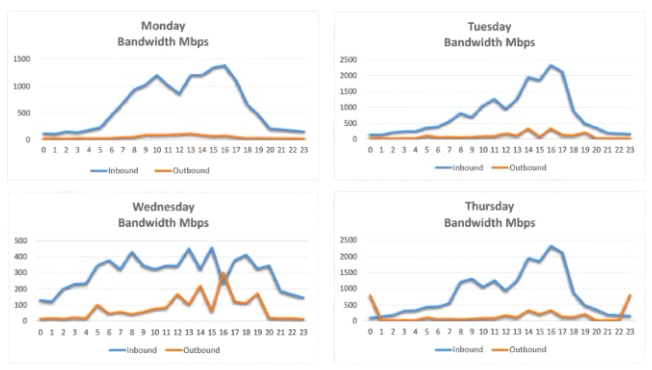
Which of the following should the analyst review to find out how the data was exfilltrated?
Options
