Free Amazon SCS-C01 Exam Dumps
Here you can find all the free questions related with Amazon AWS Certified Security - Specialty Exam (SCS-C01) exam. You can also find on this page links to recently updated premium files with which you can practice for actual Amazon AWS Certified Security - Specialty Exam . These premium versions are provided as SCS-C01 exam practice tests, both as desktop software and browser based application, you can use whatever suits your style. Feel free to try the AWS Certified Security - Specialty Exam premium files for free, Good luck with your Amazon AWS Certified Security - Specialty Exam .MultipleChoice
Every application in a company's portfolio has a separate AWS account for development and production. The security team wants to prevent the root user and all 1AM users in the production accounts from accessing a specific set of unneeded services. How can they control this functionality?
Please select:
OptionsMultipleChoice
An organization has setup multiple 1AM users. The organization wants that each 1AM user accesses the 1AM console only within the organization and not from outside. How can it achieve this?
Please select:
OptionsMultipleChoice
Attach the following SCP to the OU that contains this account:
OptionsMultipleChoice
A recent security audit identified that a company's application team injects database credentials into the environment variables of an AWS Fargate task. The company's security policy mandates that all sensitive data be encrypted at rest and in transit.
When combination of actions should the security team take to make the application compliant within the security policy? (Select THREE)
Store the credentials securely in a file in an Amazon S3 bucket with restricted access to the application team IAM role Ask the application team to read the credentials from the S3 object instead
Create an AWS Secrets Manager secret and specify the key/value pairs to be stored in this secret
Modify the application to pull credentials from the AWS Secrets Manager secret instead of the environment variables.
Add the following statement to the container instance IAM role policy
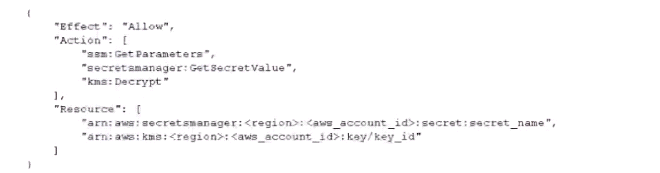
Add the following statement to the execution role policy.
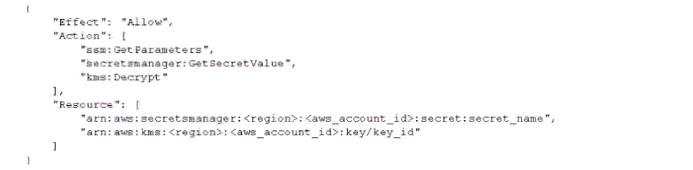
Log in to the AWS Fargate instance, create a script to read the secret value from AWS Secret Manager, and inject the environment variables. Ask the application team to redeploy the application.
OptionsMultipleChoice
A company has several workloads running on AWS Employees are required to authenticate using on-premises ADFS and SSO to access the AWS Management Console Developers migrated an existing legacy web application to an Amazon EC2 instance Employees need to access this application from anywhere on the internet but currently, mere is no authentication system but into the application.
How should the Security Engineer implement employee-only access to this system without changing the application?
OptionsMultipleChoice
A company has a website with an Amazon CloudFront HTTPS distribution, an Application Load Balancer (ALB) with multiple web instances for dynamic website content, and an Amazon S3 bucket for static website content. The company's security engineer recently updated the website security requirements:
* HTTPS needs to be enforced for all data in transit with specific ciphers.
* The CloudFront distribution needs to be accessible from the internet only.
Which solution will meet these requirements?
Set up an S3 bucket policy with the awssecuretransport key Configure the CloudFront origin access identity (OAI) with the S3 bucket Configure CloudFront to use specific ciphers. Enforce the ALB with an HTTPS listener only and select the appropriate security policy for the ciphers Link the ALB with AWS WAF to allow access from the CloudFront IP ranges.
Set up an S3 bucket policy with the aws:securetransport key. Configure the CloudFront origin access identity (OAI) with the S3 bucket. Enforce the ALB with an HTTPS listener only and select the appropriate security policy for the ciphers.
Modify the CloudFront distribution to use AWS WAF. Force HTTPS on the S3 bucket with specific ciphers in the bucket policy. Configure an HTTPS listener only for the ALB. Set up a security group to limit access to the ALB from the CloudFront IP ranges
Modify the CloudFront distribution to use the ALB as the origin. Enforce an HTTPS listener on the ALB. Create a path-based routing rule on the ALB with proxies that connect lo Amazon S3. Create a bucket policy to allow access from these proxies only.
A company Is trying to replace its on-premises bastion hosts used to access on-premises Linux servers with AWS Systems Manager Session Manager. A security engineer has installed the Systems Manager Agent on all servers. The security engineer verifies that the agent is running on all the servers, but Session Manager cannot connect to them. The security engineer needs to perform verification steps before Session Manager will work on the servers.
Which combination of steps should the security engineer perform? (Select THREE.)
OptionsMultipleChoice
Auditors tor a health care company have mandated mat all data volumes be encrypted at rest Infrastructure is deployed mainly via AWS CloudFormation however third-party frameworks and manual deployment are required on some legacy systems
What is the BEST way to monitor, on a recurring basis, whether all EBS volumes are encrypted?
OptionsMultipleChoice
A company created an AWS account for its developers to use for testing and learning purposes Because MM account will be shared among multiple teams of developers, the company wants to restrict the ability to stop and terminate Amazon EC2 instances so that a team can perform these actions only on the instances it owns.
Developers were Instructed to tag al their instances with a Team tag key and use the team name in the tag value One of the first teams to use this account is Business Intelligence A security engineer needs to develop a highly scalable solution for providing developers with access to the appropriate resources within the account The security engineer has already created individual 1AM roles for each team.
Which additional configuration steps should the security engineer take to complete the task?
OptionsMultipleChoice
A Security Administrator is configuring an Amazon S3 bucket and must meet the following security requirements:
* Encryption in transit
* Encryption at rest
* Logging of all object retrievals in AWS CloudTrail
Which of the following meet these security requirements? (Choose three.)
OptionsMultipleChoice
A financial institution has the following security requirements:
* Cloud-based users must be contained in a separate authentication domain.
* Cloud-based users cannot access on-premises systems.
As part of standing up a cloud environment, the financial institution is creating a number of Amazon managed databases and Amazon EC2 instances. An Active Directory service exists on-premises that has all the administrator accounts, and these must be able to access the databases and instances.
How would the organization manage its resources in the MOST secure manner? (Choose two.)
Options
